
Looking to offer your users a single sign-on experience from your video content?
IBM now supports using OpenID Connect (OIDC) based identity providers with its enterprise video platform. This expands the options that organizations have for user authentication to access live and on demand video material.
- What is OpenID Connect?
- Setting up single sign-on with OIDC for enterprise video
- Benefits of OIDC
- OIDC compared to SAML
What is OpenID Connect?
OpenID Connect, or OIDC, is an identity layer on top of the OAuth 2.0 protocol framework. Using JSON web tokens (JWT), the technology verifies the identity of the user and obtains basic user profile information. This is done for authentication through utilizing familiar and shared credentials, a single sign-on (SSO) methodology. These sync up with an OpenID Connect identity provider, a partial list of which include:
- ADFS (Active Directory Federation Services)
- Azure AD (Active Directory)
- IBMid (IBM identity provider)
- OKTA
- Ping
- SalesForce
- SiteMinder
In action, each time the user logs in using OIDC they are redirected briefly to a login process tied to the identity provider. After completing that process they are then being taken back to the service. In these cases, information is shared between the service and identity provider.
For example, let’s say you are using OKTA as your identity provider for your organization and you’re using IBM Enterprise Video Streaming. In this scenario the user, when trying to access restricted video content, would be prompted to login using credentials tied to OKTA. When the user authenticates OKTA sends back to IBM about the user and the authentication that was performed. That information is returned in the form of a JWT.
Setting up single sign-on with OIDC for enterprise video
Having authentication on an IBM Enterprise Video Streaming account through an OpenID Connect identity provider is a relatively quick process. It involves having an account admin login into the dashboard and go to the Account and then Security settings.
This will allow them to select the type of authentication required to access the live and on demand streaming content on the account. Options include: email verification, Google Apps SSO, SAML based SSO and OpenID Connect SSO.
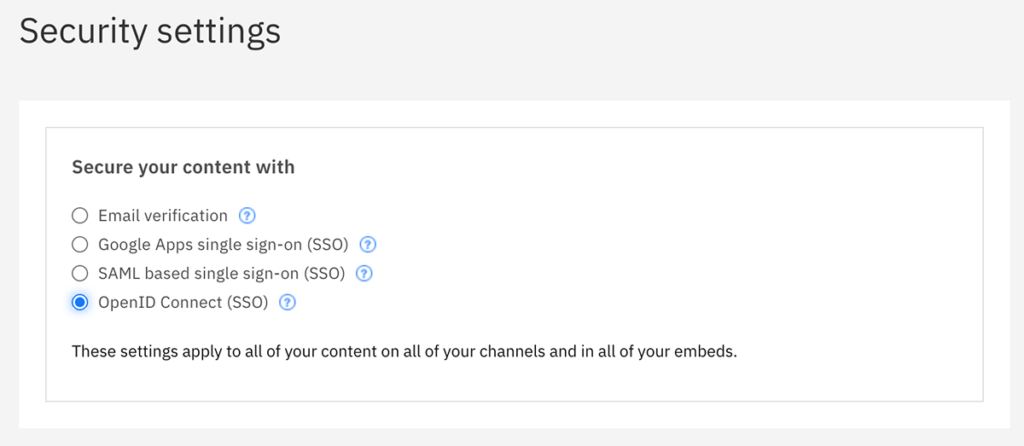
After choosing OpenID Connect, the following details will be required related to the chosen identity provider:
- Client ID
- Client Secret
- Discovery URL
After inputting these details, user authentication while now take place using credentials from the OIDC identity provider. Please consult this support article for more details on setting up OpenID Connect for your account.
Benefits of OIDC
The benefits of OpenID Connect align with the benefits of a single sign-on (SSO) approach. This method unifies several services, like accessing email or a repository of documents, so that to access them end users utilize a shared, or “single”, set of credentials for authentication.
That has an obvious benefit to the user experience, requiring less user credentials to remember. It also means less time wasted from users having to sign up for separate services. That can also trickle down to reducing costs, avoiding wasting support resources associated with resetting passwords or regaining access to accounts in many scenarios.
Besides user experience and cost, there are also debatable benefits to security. That debate is around a single password versus multiple passwords. The fear is a single password, if compromised, would grant access to a variety of services. However, generally the assumption is having a single password means that the user is more likely to select a strong password that is harder to crack. If forced to have numerous logins they might select ones that are weaker but easier to remember, or even duplicate passwords across services.
OIDC compared to SAML
Single sign-on (SSO) support for IBM’s enterprise video platform is not new. In fact, it’s been in the solution for years. The prior methods supported were through Google Apps or SAML based SSO. This update introduces another methodology through OpenID Connect.
For those curious on these technologies, both SAML and OIDC can be used toward federated identity authentication, which is using shared logins across service providers. There are differences between the technology types, though. SAML is a more mature technology, with the latest version (2.0) being introduced in 2005. It uses XML, in an XML document called the SAML assertion, for its identity data format along with HTTP for data transport.
OpenID Connect (OIDC), on the other hand, is a newer technology that was ratified as a standard in 2014. It’s an extension of OAuth2. As a result of its age, it was designed with web and mobile formats in mind. It uses a JSON format, with a JSON web token that is digitally signed, along with HTTPS for data transport.
While the process under the hood is different, both technologies are directed toward the same goal of identity authentication. Being a newer technology, OIDC benefits from being developed for a mobile audience. It’s approach of using JSON tokens in place of XML is perceived as a more lightweight data processing requirement. However, SAML has a longer history of being used for identity authentication and is already feature-rich, covering a range of requirements. So if one were to ask which was “better”, the answer would differ on the scenario. On the positive side, IBM’s enterprise video solution now supports both and so whichever approach an organization decides on can be utilized.
Summary
Single sign-on is a great method for creating a more enjoyable end user experience, allowing them to utilize familiar credentials to access content. OpenID Connect offers a way to make this possible, linking your IBM Enterprise Video Streaming account to an identity provider.
Using an OpenID Connect based identity provider already and interested in learning more about using it with an IBM video solution? Contact us.